Today we are going to have a deeper look of these different types like where they store, what they damage,and how to get rid from them?? So Guys read on...

System Sector Viruses
System sectors are special areas on your disk containing programs that are executed when you boot (start) your PC. System sectors (Master Boot Record and DOS Boot Record) are often targets for viruses. These boot viruses use all of the common viral techniques to infect and hide themselves. They rely on infected floppy disk left in the drive when the computer starts, they can also be "dropped" by some file infectors or Trojans.
Stealth Virus
These viruses evade anti-virus software by intercepting its requests to the operating system.
A virus can hide itself by intercepting the anti-virus software’s request to read the file and passing the request to the virus, instead of the OS. The virus can then return an uninfected version of the file to the anti-virus software, so that it appears as if the file is "clean".
Bootable CD-ROM Virus
These are a new type of virus that destroys the hard disk data content when booted with the infected CD-ROM.
Example: Someone might give you a LINUX BOOTABLE CD-ROM.
When you boot the computer using the CD-ROM, all your data is gone. No Anti-virus can stop this because AV software or the OS is not even loaded when you boot from a CD-ROM.
Self-Modification Virus
Most modern antivirus programs try to find virus-patterns inside ordinary programs by scanning them for virus signatures.
A signature is a characteristic byte-pattern that is part of a certain virus or family of viruses.
Self-modification viruses employ techniques that make detection by means of signatures difficult or impossible. These viruses modify their code on each infection. (each infected file
contains a different variant of the virus)
Polymorphic Code Virus
A well-written polymorphic virus therefore has no parts that stay the same on each infection.To enable polymorphic code, the virus has to have a polymorphic engine (also called mutating engine or mutation engine). Polymorphic code is a code that mutates while keeping the original algorithm intact.
Metamorphic Virus
Metamorphic viruses rewrite themselves completely each time they are to infect new executables. Metamorphic code is a code that can reprogram itself by translating its own code into a temporary representation, and then back to normal code again.
For example, W32/Simile consisted of over 14000 lines of assembly code, 90% of it is part of the metamorphic engine.
File Extension Virus
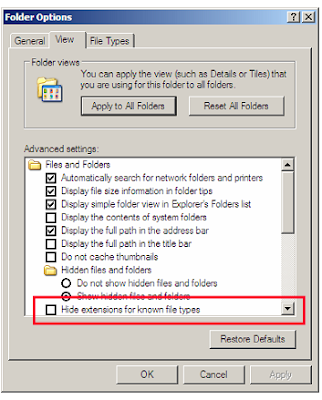
File extension viruses change the extensions of files. .TXT is safe as it indicates a pure text file. With extensions turned off if someone sends you a file named BAD.TXT.VBS you will only see BAD.TXT.If you've forgotten that extensions are actually turned off, you might think this is a text file and open it. This is really an executable Visual Basic Script virus file and could do
serious damage .
Countermeasure is to turn off “Hide file extensions” in Windows.
...........................................................................................................................................................

System Sector Viruses
System sectors are special areas on your disk containing programs that are executed when you boot (start) your PC. System sectors (Master Boot Record and DOS Boot Record) are often targets for viruses. These boot viruses use all of the common viral techniques to infect and hide themselves. They rely on infected floppy disk left in the drive when the computer starts, they can also be "dropped" by some file infectors or Trojans.
Stealth Virus
These viruses evade anti-virus software by intercepting its requests to the operating system.
A virus can hide itself by intercepting the anti-virus software’s request to read the file and passing the request to the virus, instead of the OS. The virus can then return an uninfected version of the file to the anti-virus software, so that it appears as if the file is "clean".
Bootable CD-ROM Virus
These are a new type of virus that destroys the hard disk data content when booted with the infected CD-ROM.
Example: Someone might give you a LINUX BOOTABLE CD-ROM.
When you boot the computer using the CD-ROM, all your data is gone. No Anti-virus can stop this because AV software or the OS is not even loaded when you boot from a CD-ROM.
Self-Modification Virus
Most modern antivirus programs try to find virus-patterns inside ordinary programs by scanning them for virus signatures.
A signature is a characteristic byte-pattern that is part of a certain virus or family of viruses.
Self-modification viruses employ techniques that make detection by means of signatures difficult or impossible. These viruses modify their code on each infection. (each infected file
contains a different variant of the virus)
Polymorphic Code Virus
A well-written polymorphic virus therefore has no parts that stay the same on each infection.To enable polymorphic code, the virus has to have a polymorphic engine (also called mutating engine or mutation engine). Polymorphic code is a code that mutates while keeping the original algorithm intact.
Metamorphic Virus
Metamorphic viruses rewrite themselves completely each time they are to infect new executables. Metamorphic code is a code that can reprogram itself by translating its own code into a temporary representation, and then back to normal code again.
For example, W32/Simile consisted of over 14000 lines of assembly code, 90% of it is part of the metamorphic engine.
File Extension Virus
File extension viruses change the extensions of files. .TXT is safe as it indicates a pure text file. With extensions turned off if someone sends you a file named BAD.TXT.VBS you will only see BAD.TXT.If you've forgotten that extensions are actually turned off, you might think this is a text file and open it. This is really an executable Visual Basic Script virus file and could do
serious damage .
Countermeasure is to turn off “Hide file extensions” in Windows.
...........................................................................................................................................................
...........................................................................................................................................................
...........................................................................................................................................................
...........................................................................................................................................................
...........................................................................................................................................................
Cyberspaceshield is a company with group of certified hacker, who are always ready to assist you with all your cyber problems.
ReplyDeleteWe’ve been in existence for ages now, we are reliable and helpful in terms of cyber bullying.
We can help you get all your cyber threats and bullies solved in less than what you can ever imagine.
These are somethings we specializes on:
➡️ Phone Hacks
➡️ Credit scores
➡️ Social media Hacks (Facebook, Instagram, tik tok).
➡️ Binary options
➡️ Binary Recovery
➡️ Clear criminal records etc.
The internet is full of scammers, that’s why we’re here to help you fight them out.
If you have been a victim of scam, don’t hesitate to write us on
EMAIL: Cyberspaceshield@gmail.com
Thank you!!!
Guy's Whats-up !
ReplyDeleteDo you wanna learn Hacking/Spamming/Carding ?
Do you wanna start your earning from home ?
Here I'm..
I'm offering complete packages, for Learning:
Hacking , Spamming, Carding, Spying etc
*Legit & Valid Tools & tutorials Stuff.
Contact 24/7
Tele-gram = @leadsupplier
Skype/Wickr = peeterhacks
I'C'Q = 752 822 040
All Type of Tools Available
MAILERS
SENDERS
KEY LOGGERS
KALI LINUX FULL
BTC CRACKER/FLASHER
BOMBER
VIRUSES
SHELLS
BRUTES
CPANELS
HACKING TUTS & STUFF
CARDING METHODS FOR CASHOUT & SPAMMING
FB/WA HACK TIPS & TRICKS
ETC
Fresh Fullz are available too
CC FULLZ
SSN DOB DL FULLZ (BULK QTY)
HIGH CS FULLZ (700+)
PREMIUM FULLZ
SBA/PUA/UI FILLING FULLZ
EMPLOYMENT FULLZ
BUSINESS FULLZ
Get In Touch :
Skype/Wickr = peeterhacks
I'C'Q = 752 822 040
Tele-gram = @killhacks
Fresh Spammed & Verified
Invalid stuff will be replace
Bulk order preferable